In the past few months, we have noticed a huge uptick in smishing attacks targeted at small and medium-sized businesses. To help you combat this growing threat, we have written this guide that shares everything you need to know about smishing and how to protect yourself from it.
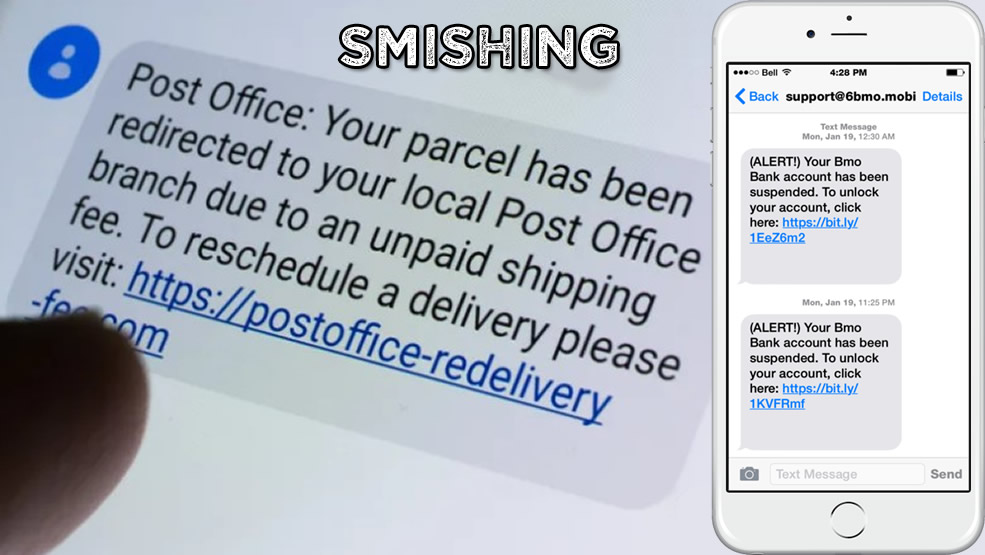
WHAT IS SMISHING?
Smishing is a type of phishing attack that uses phones as the primary medium of attack. The term “Smishing” is formed by combining “SMS” (short messaging service) and “phishing”. Smishing is a relatively low-tech cyberattack that relies heavily on social engineering techniques. But it can also be assisted by malware or fraudulent websites.

Like in phishing attacks, the perpetrators of smishing also pose as legitimate businesses, authority figures, or representatives of institutions such as a bank, tax services, tech support, etc. The goal of such attacks is to elicit sensitive personal information, login credentials, banking details, credit card numbers, etc. The gathered information is then utilized to commit financial fraud, identity theft, or launch further cyberattacks.
HOW DOES SMISHING WORK?
Smishing employs social engineering techniques to manipulate the victims into performing malicious actions or divulging sensitive information. These attacks use deception and fraud to drive trust by posing as legitimate organizations or individuals to lower the victim’s natural defenses against threats.
The attackers also use context and personalization to make their messages look genuine. Finally, they try to heighten the victims’ emotions by using fear of authority or time sensitivity, forcing the victims to act quickly without thinking about the actions or following company procedures.
Typically, a smishing attack involves an attacker disguised as a trusted entity such as a package delivery service, IRS, etc., and using a spoofed phone number, sending a text message to the victim. The recipient is instructed to click on a link within the text message that leads to a fraudulent website where they are asked to enter their private information.
So, a smishing attack is comprised of three basic phases:
- Distribution of malicious text messages to the targets
- Information extraction from the victims using social engineering
- Use of that information for financial gains or further malicious activities
WHAT MAKES SMISHING DANGEROUS?
Smishing attacks are dangerous because they are easy to carry out and have higher chances of success because of the following reasons:
- People are much more likely to read and respond to text messages than emails. According to a Gartner report, people read 98% of text messages and respond to 45% of them.
- It is easier to acquire targets for smishing attacks as compared to phishing emails. For phishing attacks, attackers need email addresses, which are often difficult to guess. But attackers can send smishing messages on a large scale without knowing any phone number. They can simply come up with any combination of digits that is the same length as a phone number.
- Attackers can use cheap, disposable prepaid phones and email-to-text services to hide their identities.
- Attackers can use spoofing to disguise their phone numbers.
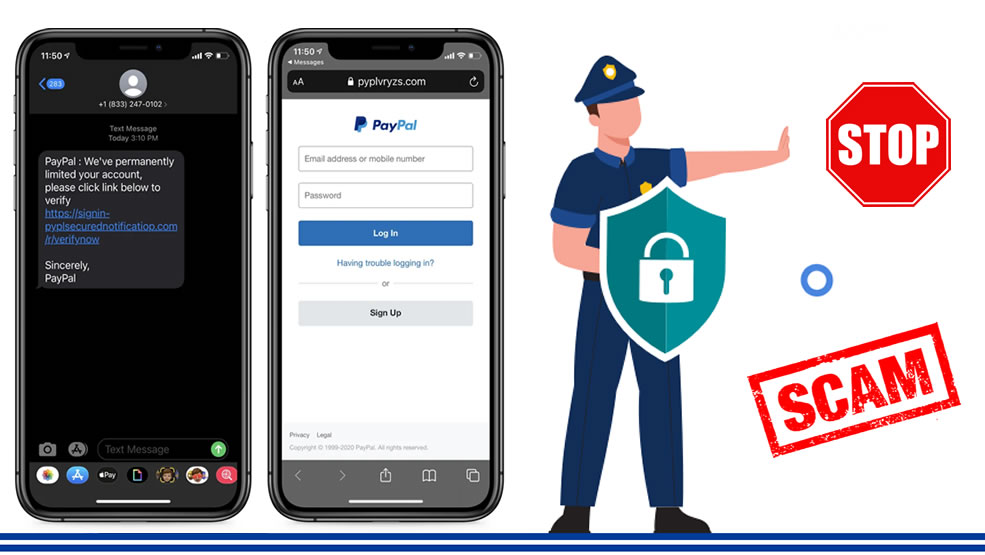
Another danger of smishing is that if you, unfortunately, fall victim to smishing, you are in danger of further attacks because the attackers usually sell the phone numbers of victims as legitimate targets to other malicious actors.
TYPES OF SMISHING
TEXT PHISHING
Most of the smishing attacks fall into this category. In text-based phishing, the main goal of the attacker is to get the recipient to either click on a malicious link or call a phone number provided within the text message. Some smishing messages may direct the recipient to perform certain actions, such as purchasing gift cards and sending the details as a response to the text message.
VOICE PHISHING (VISHING)
Vishing is another form of phishing that primarily uses voice calls for the attack. The term “vishing” is formed by combining ‘voice’ and ‘phishing’. In this type of attack, the scammers pose as representatives of financial institutions, law enforcement, tech support, or an employer and use social engineering to elicit personal information and financial details.
Scammers can place hundreds of vishing phone calls using Voice over Internet Protocol (VoIP). They also spoof the caller ID to make the phone call appear to come from a trusted source.

INSTANT MESSAGING PHISHING
Instant messaging phishing uses social media services such as Facebook, Twitter, etc., and instant messaging such as WhatsApp and Telegram, to perpetrate phishing scams. The attackers rely on the fact that people are more likely to open and respond to messages received on instant messaging platforms.
Like any other phishing attack, the goal of instant messaging phishing is also to elicit personal information such as passwords, credit card numbers, financial information, etc. Most of such messages are spam coming from strangers’ accounts. But some targeted instant messaging phishing attacks use spoofed or hacked accounts.
EXAMPLES OF SMISHING
The context of smishing messages is usually rooted in everyday events and that makes such messages difficult to notice right away.
Here are a few examples of the context of smishing messages:
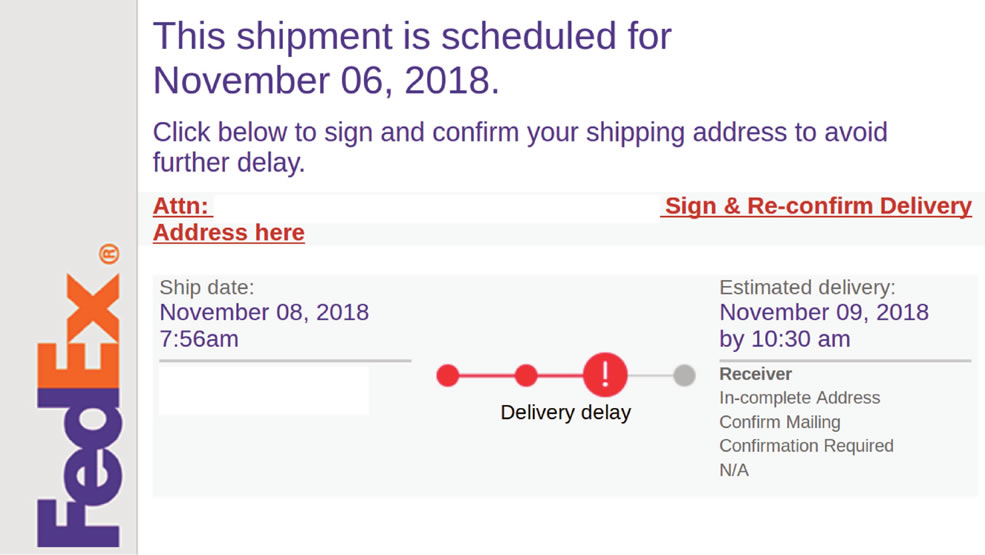
Nowadays, most people rely on e-commerce websites for their shopping needs. This means that a lot of people are always waiting for packages to arrive. And companies usually notify customers of package delivery updates via SMS.
This has led to the rise of package delivery smishing messages that ask the recipients to click on a malicious link to track their package. The senders make it look like the message came from reputed well-known companies such as Amazon, DHL, UPS, etc. and the malicious link is disguised as a package tracking URL.
To hide the true destination of the URL, the scammers either use URL shorteners or create domain names that are similar to the legitimate ones.
PASSWORD RESET SMISHING
This type of smishing attack targets users whose emails have been compromised. The attacker sends a text message to the user claiming that their email account was breached.
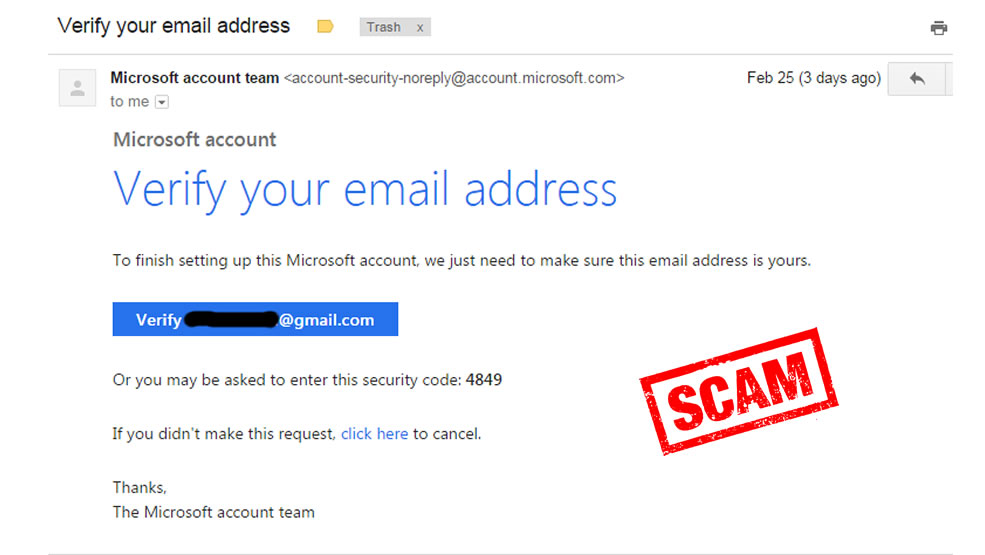
In the meantime, the scammers use the “forgot my password” option that sends a Two-factor authentication (2FA) code to the victim’s phone. Then they ask the victim to share their 2FA code and use it to gain access to the victim’s account.
TAX SEASON SMISHING
Tax season comes with not just the stress of filing your taxes but also the threat of smishing scams. Lots of paperwork and looming deadlines for tax filing can cause stress and anxiety and the scammers try to take advantage of it.

There are two common tax season smishing scams:
- The first kind of scam claims that the recipient owes money to the IRS and directs them to a fraudulent payment website. This kind of smishing message uses scare tactics to induce fear and force the victim to act quickly.
- The second kind of scam claims that the victim is entitled to a tax refund and invites them to click on a link to claim their money. The link either takes them to a fraudulent website designed to steal their financial information or install malware on their device.
CEO FRAUD SMISHING
Employees do not usually receive messages directly from their CEO or someone from senior management. But when they do, it can engender some strong reactions. Some may jump at the opportunity, eager to impress while others may be scared stiff thinking, they may make a mistake.

In any case, scammers rely on such sentiments to escape the scrutiny of the requests made in their messages. Such smishing messages are carefully crafted to create a sense of urgency, which coupled with the engendered sentiments can compel employees to respond to such smishing messages.
BANK TEXTS SMISHING
Communication from financial institutions is always a potent context for smishing attacks. It is a common practice for banks to notify their customers of transactions via SMS. So, scammers very often disguise their smishing messages as communication coming from banks.
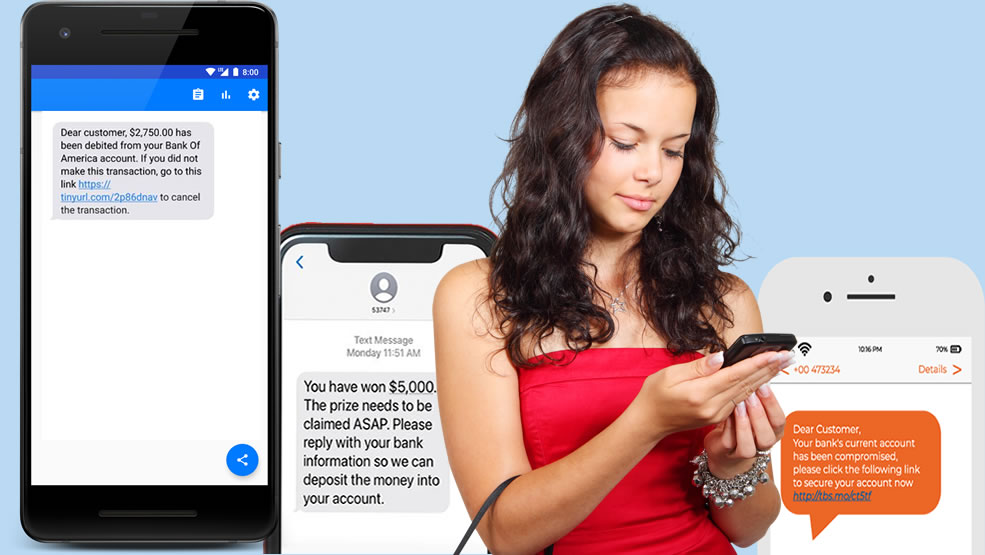
Generally, they use the pretext of unpaid bills, suspicious transactions, account or card cancellations, etc. to create a stressful situation for the recipient and force them into clicking malicious links or sharing sensitive banking information.
ARE SMISHING MESSAGES TARGETED?
A majority of smishing attacks are automated robocalls and spam messages. However, recently we have noticed an uptick in targeted smishing attacks. The scammers select targets based on their affiliation to organizations or universities, relationships with specific banks or financial institutions, or purchase history with certain e-commerce sites.

CEO fraud is the most commonly used smishing variant when targeting small and medium-sized businesses. Targeted smishing messages are carefully crafted using the name of the CEO as well as that of the recipient. Such smishing messages are usually readily identified due to spelling and grammatical errors. They also use a tone or language that is not consistent with the company culture.
HOW TO PROTECT AGAINST SMISHING?
Theoretically, smishing attacks are easy to protect against. Smishing cannot cause any harm if you do not take the bait in the messages. So, you will be absolutely fine if you do nothing.
However, doing nothing is easier said than done. Users receive tens if not hundreds of legitimate messages every day and it is not possible to ignore them all. But users can protect themselves by keeping the following in mind:
1. DO NOT RESPOND
Do not engage in any way with messages that you were not expecting, especially those asking you to click, call, or respond. Any response to smishing messages signals the attackers that your phone number is active and paints a target on your back for future attacks.
2. CALL YOUR BANK DIRECTLY
Banks and other legitimate institutions never ask for login credentials or other sensitive information via text. If you receive any message that you deem suspicious, call the bank directly on a phone number published on their website. Never call the phone number provided in the text message.

3. DO NOT CLICK ON LINKS WITHIN MESSAGES
Never click on links in text messages, especially ones that have been shortened. If necessary, reach out to the bank via known official channels.
4. NEVER SHARE PASSWORD OR MFA CODE
Multi-factor authentication (MFA) protects your accounts by adding an extra security layer. Even if your username-password combination is exposed, MFA prevents account access unless thanks to the additional authentication factor.
Two-factor authentication (2FA) is the most commonly used MFA variant. Often the second authentication factor is a verification code sent as a text message. Never share this code with anyone. Legitimate organizations and tech support will never ask you to share the 2FA code.
It is also advisable to move away from text message-based verification and use dedicated verification apps such as Google Authenticator.
5. SLOW DOWN; NEVER ACT IN HASTE
One of the most common tactics that scammers use is creating a sense of urgency. Their goal is to force you to act quickly and not to allow you time to evaluate their request/demand. Messages that claim to be urgent or offers valid for only a limited time are usually signs of smishing.
6. REPORT IT TO YOUR IT TEAM
Report suspicious messages to your IT team. They will be able to confirm whether or not the message is actually a smishing attack and alert your colleagues about the smishing messages.
7. BE VIGILANT; LOOK FOR SIGNS OF COMMON SMISHING MESSAGES
Your most important weapon against smishing is awareness. You can stop smishing attacks dead in their tracks simply by identifying and not engaging with such messages.
WHAT TO DO IF YOU GET SMISHED?
First things first, always be skeptical of text messages from unknown numbers asking you to perform tasks. SMS is a notoriously insecure method of communication so treat it as such.
If a message is suspicious, check with the person or organization the sender is claiming to be via known official channels and confirm it was actually them.
Reach out to your IT team. If you are a client of ITE DATACOM, you can reach out to us via our Support Page by submitting a ticket.

If your IT team confirms that the message you received is a smishing attack, you can block the number.
Last, always note the sender’s phone number and save a screenshot of the message so you can pursue a complaint with the Federal Communications Commission (FCC), Federal Trade Commission (FTC), and National Phone Number Registry (NPNR).
HOW TO SUBMIT A COMPLAINT ABOUT SMISHING
The FCC, FTC, and NPNR provide mechanisms for reporting smishing threats. Reporting the smishing incidents directly to these organizations helps prevent their proliferation.
If you’d like to take action yourself, you can report the sender’s number in a few places:
- Enter the phone number in the National Phone Number Registry, then enter a comment about the number, for example, “I received a smishing message from this number”
- Navigate to the National Do Not Call registry in your browser and fill out the form along with the details of the received message.
- Navigate to FCC – Consumer Inquiries And Complaint Center in your browser and fill out the form along with the details of the message. Make sure to select “Unwanted Calls/Messages (including do not call and spoofing)” under the “Phone Issues” section.

CONCLUSION
That’s all you need to know about smishing… NOT! Like phishing, smishing scams are getting more frequent and difficult to identify, especially for busy employees. Your best defense against smishing is awareness. So, stay up to date on the latest smishing, phishing, and other similar threats to keep yourself safe.
We are here to help.
If you are a ITE DATACOM customer, feel free to reach out to your dedicated consultant to schedule a Cybersecurity Awareness Training and learn about phishing, smishing, and other common cyberattacks.

Call or email us today. Info@Itedatacom.us 305 490 8331.


Add a Comment