If you use a computer, you need to care about malicious software. Malicious software is any piece of code designed to harm a computer system and it has been around for a very long time. Viruses have only become more sophisticated and costly, but there are many options for protecting yourself and your business from attack.

The basic steps for a more secure system include using complex passwords (or even better, a password manager and two-factor authentication), utilizing antivirus software, and updating your system regularly. This, however, is the absolute least you can do to protect yourself online. Ideally, you are preparing for the imminent disaster that is someone in your organization accidentally downloading ransomware which holds your server hostage. It happens, and you should be prepared. Knowing a little bit about viruses and planning ahead will take you a long way.
HOW TO GET MALWARE
Malware, short for malicious software, is a blanket term for the endless number of nasty software programs lurking the web and waiting for an opening to take hold of your system. Malware includes viruses, worms, trojan horses, keyloggers, ransomware, spyware, and more. It takes just one virus installing itself on an end user’s computer to potentially spread across the entire network of your company. The most common attack vector for viruses is email, which is why it is critically important to prevent spam from reaching your users in the first place. If a virus is successful in gaining access to the computer, it can exploit changes in user privileges, gain access to sensitive info, monitor user activity, and perform other malicious actions.

Email is not the only way for malware to gain entry, however. Malicious software can infiltrate your computer from a number of actions, such as downloading files and programs, visiting unknown links, pirating media, or using an infected disk or drive. You can even get malware from plugging a USB drive you found on the bus into your computer or visiting sites you probably shouldn’t use at work anyway.
Contrary to what you have been told, you don’t even need to knowingly download files to get a virus. You can click the wrong link or ad and kick off a chain of events that could compromise your machine, or worse, your entire company. Some malware is even file-less. There often isn’t a clear indicator of malware being present on your system, but when error messages appear for no apparent reason in software programs that previously worked just fine you should be suspicious and get in touch with your IT department.
Some small changes you can make today include avoiding sites known for propagating viruses, checking with your IT department before downloading, and using an adblocker. We recommend Ublock Origin at the time of this writing. If you have never used an adblocker before, keep in mind that some sites, like Forbes.com, will either withhold content or not work unless you turn your adblocker off. All you have to do is click the extension to turn it off while you visit those sites. Unfortunately, there are still many sites that put ad income before security, so it’s a minor annoyance you may have to deal with while using an adblocker.
“Malicious software can infiltrate your computer from a number of actions, such as downloading files and programs, visiting unknown links, pirating media, or using an infected disk or drive.”
Asani Ali – AsaniAli.org
SPYWARE

Spyware is exactly as creepy as it sounds: software designed to silently track your activities as you use your device. The end goal of spyware is to collect information valuable to the attacker, such as your passwords, account numbers, or even your daily communications. Spyware is interesting because it’s increasingly used in political espionage and undermining the efforts of activists. However, when it comes to a business, the end goal of spyware is most likely to steal financial information and passwords. Nasty stuff.
RANSOMWARE
Ransomware is a form of malware that installs secretly on a victim’s computer and takes it hostage. Once installed it executes a cryptovirology attack on the system and demands a ransom payment to restore what’s affected. This past year has seen a slew of ransomware attacks by Cryptolocker and Cryptowall, but there are other types out there such as Locky, Crysis, Petya, Cerber, and RAA. Simple ransomware may lock the computer user out and display a message requesting payment to unlock it. More advanced malware encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them. The ransomware may encrypt the computer’s entire hard drive or just a certain set of files. Simply put, ransomware is a denial-of-access attack that prevents computer users from accessing files because it is nearly impossible to decrypt the files without the decryption key. Ransomware attacks are typically carried out using a Trojan that is disguised as a legitimate file. For example, an attacker might mask their malware as a resume document. They will then target companies on a hiring binge hoping to trick a user into downloading and opening the harmful file.
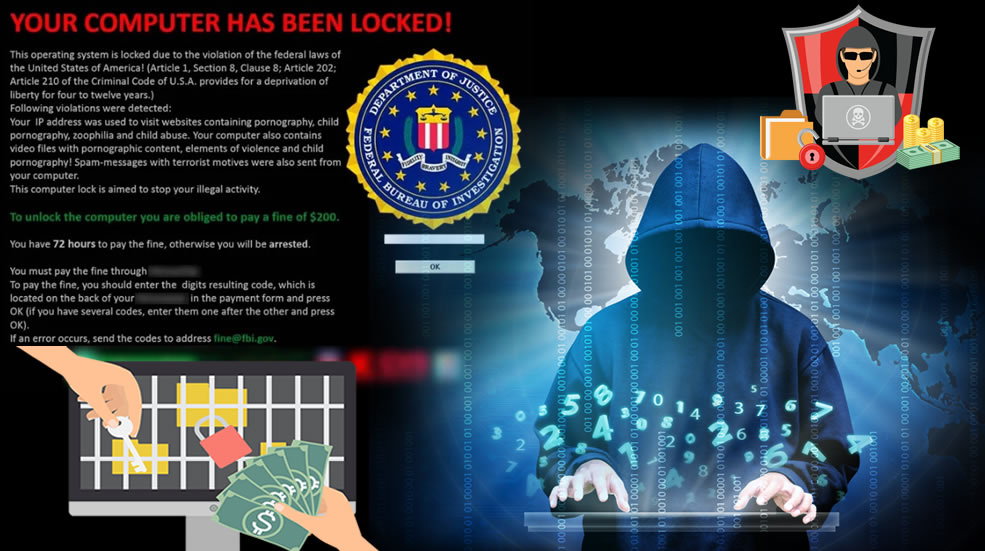
Ransomware is most troubling as it simply needs to get a foothold on a single computer to get into the server and encrypt data across an entire organization. More worrisome is that in many cases all a company can do is pay the ransom or if they are lucky enough to have all of their data backed up, reset their computers to the state they were in before the attack. In some rare cases, there are decryption tools available, but they are rare and entirely dependent on the strain of ransomware you have. We have an entire plan devoted to handling ransomware attacks that we deploy if any of our clients are affected, but the best course of action is to try and prevent an attack from taking hold in the first place by educating employees and backing up regularly.
HOW TO PREVENT MALWARE

An ounce of prevention is worth a pound of cure, and this saying is especially true in security. For all of our clients, we take a proactive approach to prepare for attacks before they happen. This includes:
- Antivirus on all computers – Webroot Antivirus is our favorite antivirus at the moment. We also implement Malwarebytes & Flushot in cases where it is needed.
- Crypto prevent on all computers – A set of scripts that we manage and deploy via our monitoring agent that blocks some malicious executables from running in the first place.
- Firewall – A well-implemented firewall is really good at blocking the bulk of common threats. You want to make sure that your firewall can do deeper threat analysis, like virus filtering, to detect common traffic patterns of attacks and stop the attacks before they get to an end user’s computer on your network.
- Restrict Access – Not every person in your organization needs admin access or the key to your physical mail server. A good rule of thumb is if someone isn’t trained in proper security practices, they probably should just have access to the files they need instead of the entire server.
- Backup. Backup. BACKUP. – While we’ve never seen a computer with Webroot and Cryptoprevent get infected with ransomware, it certainly is possible that it could happen. Generally, the only way to recover from one of these attacks, assuming you don’t pay the ransom, is to restore from backup.

Carbonite is a great secondary backup service, but we don’t love it as a primary backup. It only backs up files and it only retains versions for so long. Since it is file only, it won’t back up your server settings or your FileMaker database. Mass restorations are also really slow since all of the data has to be downloaded from the cloud during a restore. We recommend getting an image-based backup system that backs up a complete image of your server, including all files, applications, databases, and settings. ShadowProtect and Datto are the two solutions we recommend.
Security is really hard. So hard, in fact, that it is a concern many companies come to us with at first. We invest a large portion of our time in staying informed and pass our findings onto our customers. Computer viruses propagate at breakneck speed and it’s important to stay current. As always, we are here to answer your questions about security and help find a plan that works for your business.
Call Us Now to talk about security. We are here to help.

Call or email us now. info@itedatacom.us, 305 490 8331

Add a Comment