There are several common and, unfortunately, frequently successful avenues of attack that cybercriminals can use to part you from your personal contact and financial information. These phishing attack methods include email, phone calls, corrupted software or apps, social media, advertisements, and even direct SMS (text) messages.
Beyond the medium used to reach you (which is most often email—still!), what are some of the signs and behaviors to look for? Not every threat is as obvious as you’d hope, and conversations that focus on the inbox only are completely inadequate in the harrowing landscape we now find ourselves in.

1. Your software or app itself is phishing
Even the most recent headlines indicate counterfeit software and apps are still real and present dangers for digital nomads. On both Android and iOS, unscrupulous coders periodically find ways to circumvent the approval process and deliver an app that seems to provide ordinary functionality even as it siphons personal information and sends it to parties unknown.
There are other means of deception, too. Fake reviews on app stores are still astonishingly common. Several hundred or even a couple thousand glowing reviews give a surface-level impression of legitimacy, but a closer look will reveal similar phrasing used by multiple users or even suspiciously similar usernames.
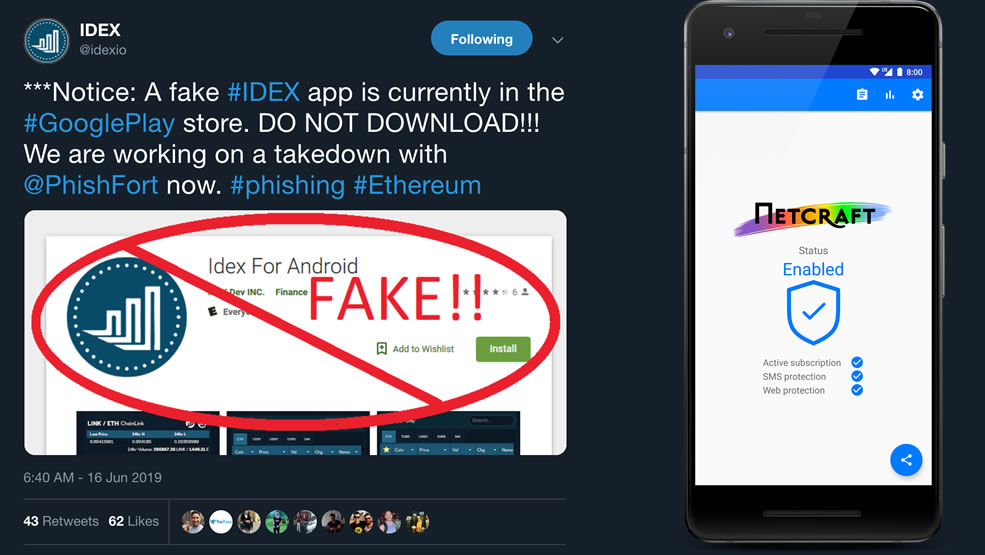
Sometimes, all it takes is a pretty user interface to rope in unsuspecting app store users. In some cases, dishonest developers might even improve on the UI of the app they’re trying to spoof, for that extra little boost of trustworthiness.
2. You’ve received a mysterious text or call
Much of the focus of social engineering remains on email, but it would be a mistake to discount smishing (SMS message phishing) and vishing (voice phishing). Would-be troublemakers can easily spoof local area codes you might recognize, or they might even pose as technical support representatives to encourage you to give up the credentials for your devices or accounts.

This is one of the oldest tricks in the books—and it’s still working. Thankfully, telling a real company dispatch apart from a fake one is usually fairly easy. Many companies, such as Microsoft and the IRS, are clear about never making unsolicited contact with customers over the phone. If you get a call from somebody offering help you didn’t ask for and don’t need, hang up immediately and block the number in your phone’s settings.
3. You’ve “won” something
Lottery scams and those ubiquitous “You’ve Won Something Glorious!” pop-up ads are still a popular way to phish for people’s bank account and routing numbers. Unfortunately, the fact they still exist and are so common means they still work. We all know that rush of adrenaline and excitement when we receive something when we least expect it.

A victim might receive a message on a fraudulent website indicating they have won a cash prize or a lottery drawing they did not enter, and that their winnings are available for direct deposit. If you get a message like this one, delete it (unread) and block the email address and/or phone number.
4. Your social media accounts are being weaponized
Social media has given rise to particularly nasty forms of “spear phishing”—that is, mining victims’ public profiles for useful information, and then posing as somebody you know, or who you at least might mistake as legitimate. Remember to vet your digital friends carefully.
Another way social media might be weaponized is through game mechanics, including surveys and questionnaires. You might be encouraged to spin a wheel, interact with the screen, or provide feedback on something, after which you’ll “win” the game and be asked for additional information.

As far as surveys go, remember that if you’re not obviously a customer, you’re probably the product. It might not surprise you to learn this, but fake surveys are so common on Facebook that users frequently light up the social site’s official message boards asking about individual questionnaires—even the rare legitimate one—where users receive compensation for providing their opinion.
At its most devious, traps like these fuel social engineering efforts like those conducted by Cambridge Analytica during the Brexit campaign, as well as by domestic and foreign actors during the 2016 presidential election.
5. Your URL doesn’t look right
No matter how you come into contact with a phishing scheme, there’s a good chance part of the action they want you to take involves visiting a specific URL. Knowing how to tell when a URL isn’t genuine or isn’t affiliated with the person or company claiming to contact you, is a critical skill.
The logical first step is to run a Google or Bing search for the company and view the top results. The URL you’ve been given should match what appears at the top of a search results page. Some browsers even give you a hand with this.
Apple’s Safari truncates the address in the URL bar to just the main domain and sub-domain as appropriate. The idea is to cut out the numbers, letters and other filler to let you know immediately if you’re somewhere you didn’t expect to be. Phishers have made an art of using long and convoluted URLs to hide their intentions.
Another thing you can do is maintain an address book with the official URLs, contact numbers, and email addresses of the companies you do business with. You might also write some rules or filters, so your inbox automatically weeds out and discards incoming messages based on trust symbols you’ve already identified, such as questionable sender addresses.
6. You’ve been warned or given an ultimatum
This is another type of scam that’s as old as the digital hills, and one that preys on the human element of fear, or the innate worry of missing an important deadline.
Scammers love to include vaguely threatening language in their phishes in order to illicit a fast, irrational response from their targets. For example, a negative message campaign might include a script that tells users their information has been compromised, and they had better hand over payment before the scammers leak that (sometimes scandalous) information to the public. A classic case of extortion.

However, you’re more likely to compromise yourself by reacting too quickly to a false threat than you are to actually have been locked out of your system, or whatever the claim is.
Do You Feel Prepared?
Living a digital life isn’t really optional anymore—not when our entire professional, social, and even political lives unfold online.
Even daily browsing can feel like a minefield, but hopefully, you feel better prepared to handle the quintessential threat that’s at the heart of nearly every malware attack today: phishing. Scam artists know how to reel in their victims, even if they’re outside the email pool. So, guard your apps, your social media, your mobile devices, and your browsers well!

If you have questions about Phishing, we are here to help. Call or email us today. Info@Itedatacom.us 305 490 8331.


Add a Comment