WELCOME TO PHISHING 102!
In part 1 of our phishing blog series, we talked about how to identify a phishing email and what to do in case you are phished. Following the simple guidelines described in the blog will keep you safe from a vast majority of phishing attempts. As we mentioned in our previous blog, with the advancement in technology, cyber-criminals are also becoming more advanced in their attacks. While most of the phishing attempts via emails are identifiable, there are a number of other phishing techniques that can prey on unsuspecting users.
When it comes to tackling the menace of phishing, knowledge is power. Being informed about the different types of phishing will help you in identifying such attacks and help protect yourself, your family, friends, and your company from phishing attacks.
WHAT ARE THE DIFFERENT TYPES OF PHISHING?
While there are a number of techniques, here are the most common and troubling ones:
1. SPAM
Spam email is the most common form of phishing in which the same email is sent to millions of users. The main aim of such emails is to elicit sensitive information that can be used for identity theft or other illegal activities or offer big rewards in exchange for small payments.

PREVENTION
If you see an email that seems too good to be true, simply mark the email as spam. Also, make sure to never click on any links or respond to the sender. This will teach your email system to automatically move such emails to the spam folder for the next time.
” If you are not sure about an email, don’t open it. If it sounds too good to be true, nine times out of ten it is not true.”
Asani Ali – AsaniAli.org
2. SPEAR PHISHING

This is a more targeted approach to email phishing. Cybercriminals research their targets, usually a company or institution, and send targeted emails to specific individuals. The emails are personalized and appear to come from senior management or from the IT/Finance department and carry a sense of urgency. This increases the likelihood of the users falling into the trap.
PREVENTION
We talked about the above two in our previous blog here, where we list the ways to identify spear phishing emails as well as remedial steps. In essence, proceed with caution when faced with urgent requests for cash and/or sensitive information. You’ll want to mark the message as spam; never click on links or respond to senders.
3. WEB-BASED DELIVERY
Web-based delivery or “man-in-the-middle,” is a sophisticated technique. In this method, the hacker places the phishing system in between the legitimate website and the user. As the user passes his/her information, the phishing system gathers it without the knowledge of the user. If you have watched the episode “Hooli-Con” from the 4th Season of Silicon Valley, you know exactly what we are talking about.
PREVENTION
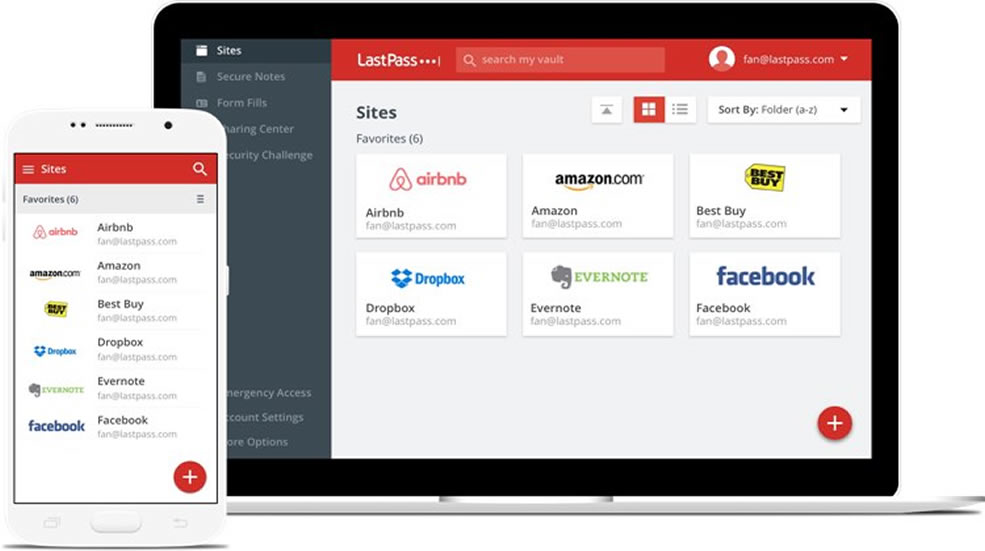
A multi-layered security system is your best defense against such attacks. Do not worry, it is not as complicated as it sounds. Multi-layered security consists of an OTP (one-time-password) in combination with a memorized password. We recommend using a password manager such as LastPass with Google Authenticator since memorizing passwords for all your business, personal, and social apps can be rather taxing on your memory. The 2FA/T-FA (two-factor authentication) is a great tool that provides this layered security.
4. LINK MANIPULATION
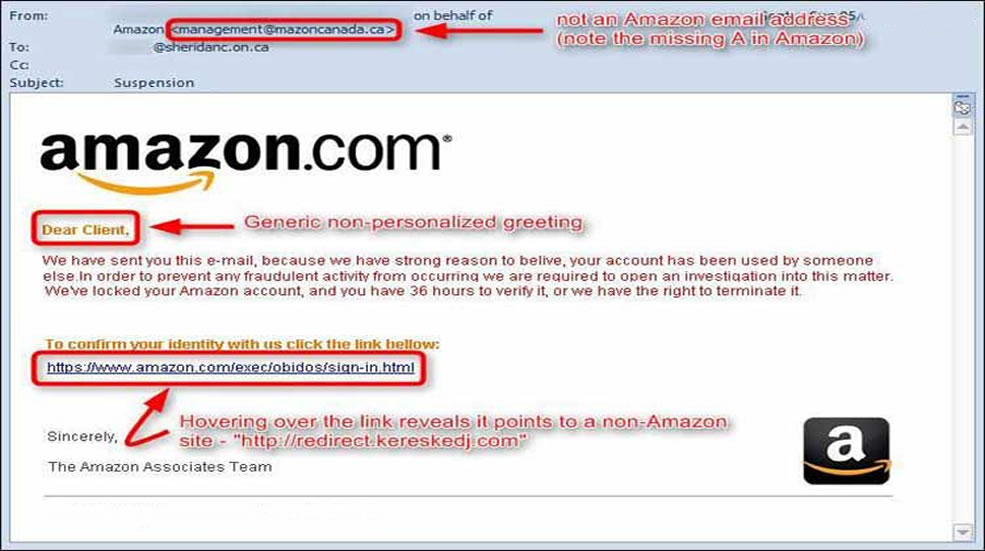
A large number of phishing attacks use link manipulation to make a link in their email appear to belong to a genuine organization. It is quite common that such links are deliberately misspelled to closely resemble the genuine website, or use subdomains of the spoofed organization, for example, www.bankofamerica.support[.]com.
PREVENTION
Hovering the mouse pointer over the link will reveal the actual address and prevent you from falling into this trap. Moreover, before entering your details into any page, be sure to check that it has “https://” and green padlock symbol in the address bar. Your best bet is to navigate to your desired website by typing it out yourself bypassing any bad links.
5. KEYLOGGERS
Keylogging or keyboard capturing is the action of covertly recording the keys struck on the keyboard. The recorded information is then deciphered by the hacker and any sensitive information found is used for their illegal activities. Keyloggers can be difficult to deal with as they come in many forms including hardware keyloggers.

PREVENTION
Password managers and automatic form fillers are helpful to a great extent. One-time passwords (OTP) or Authenticator tools such as Google Authenticator are also very handy as the passwords/keys are valid only for a limited time and the hacker will not be able to access your account using it. Using onscreen keyboards or speech-to-text conversion can also thwart most keylogger types.
If a keylogger is installed on your system, the phisher will have to make a network connection in order to retrieve the keystrokes captured by the keylogger. This connection can be prevented by a network monitor a.k.a reverse-firewall, which alerts your IT team whenever an application tries to make a network connection.
6. TROJANS
A trojan is a malicious program that misleads the user with an action that looks legitimate but actually allows unauthorized access to the user’s account. Once it gets installed, all your data and your entire system is at risk. Trojans are usually spread through email attachments that are executed by unsuspecting users. Once installed, the Trojan allows the hacker access to the infected computer. Further, ransomware attacks are also orchestrated using Trojan.

PREVENTION
Keep your computer updated with the latest software patches and software fixes as soon as they become available. This will safeguard you to some extent by blocking attackers from being able to take leverage software flaws (vulnerabilities) that otherwise could be used to break into your system. Unfortunately, antivirus software recognizes only the known trojans and they fail to recognize new, unknown Trojans.
7. MALVERTISING
Malvertising is malicious online advertising that contains scripts designed to download malware on your computer. Such ads can be inserted into legitimate and reputable websites and therefore have the potential to reach a large number of users. The scary thing about this form of phishing is that the computer can be infected without the user even clicking on the ad, or a pre-click malvertisement. Malicious code often hides undetected, and the user has no idea what’s coming. A post-click malvertisement upon clicking takes the user to a malicious site or the computer is directly infected. Such malware is usually disguised as Flash files that are quite popular.
PREVENTION
In order to safeguard yourself, keep your Adobe Reader and Flash Player updated. Instead of clicking on links, visit the Adobe website directly in order to update. Use ad blockers to prevent chances of being exposed to such ads and finally, keep your antivirus updated.
8. SESSION HIJACKING
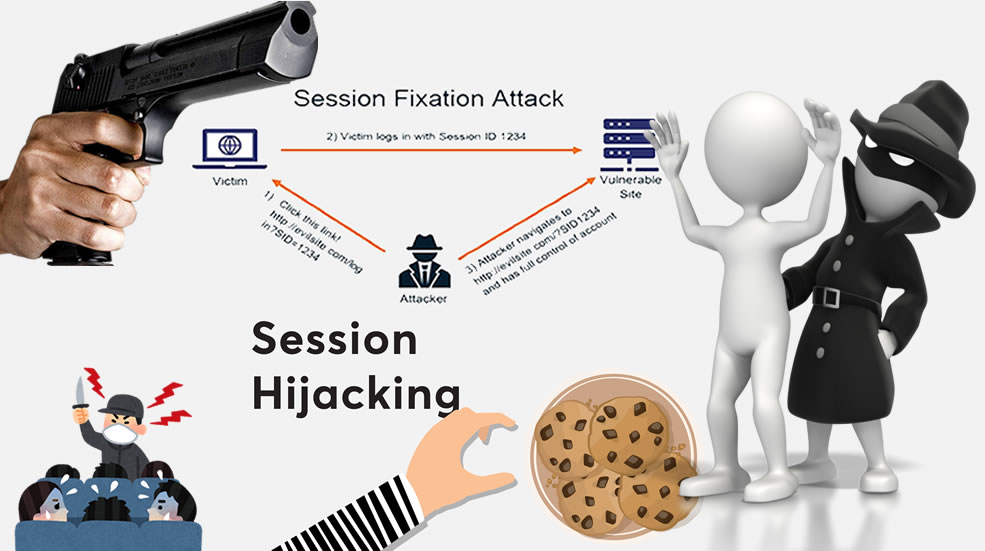
Session or cookie hijacking is the exploitation of a valid computer session to steal information from the user. In simple terms, the attacker can steal the HTTP cookies used to maintain a session on many websites by using an intermediary system or by gaining access to the cookies stored on the user’s computer.
PREVENTION
Most of the onus of preventing such attacks depends on the websites. Encryption of the data traffic is one of the ways that websites try to deal with it. As a user, remember to log out of websites whenever you are finished using them and clear your cookies. Additionally, remember to only navigate to sites using “https://” and that have the green padlock symbol in the address bar. You’ll also want to take special precautions while using public WiFi networks (e.g., cafes & airports); always make sure to turn on your VPN connection (from your workplace or 3rd party) and avoid working on sensitive items while online away from your home or office.
WHAT YOU CAN DO TO BE SAFE FROM PHISHING
- Keep your Operating System and Antivirus updated.
- Run regular, scheduled scans with your antivirus and use the auto-update facility.
- Secure your office & home network. Ask our network experts how you can do this.
- Back up your files. If you ever get infected by malicious software, you can restore your system and have your data safe.
- Use a strong password. It is advisable to use a password manager (such as LastPass) and an authenticator (Google Authenticator).
- Before entering your details into any page, be sure to check that it has “https://” and a padlock symbol in the address bar.
- Beware of open public networks in cafes & airports; connect to your VPN and be careful about working online with sensitive information.
Dealing with a virus, or malware infection in your computer is annoying, frustrating, and time-consuming. The phishers and hackers are always on the lookout for new ways to exploit your computer and/or network. For many of them, developing these programs is their full-time job. We may not always be able to remain ahead of their technology, however, we can be knowledgeable of our vulnerabilities and always be cautious. Remember, knowledge is power, and always think before you click.
So how worried are you about phishing in your personal and work life? We offer Security Plans and Phishing Audits to protect and educate your staff in case of an attack in addition to having Secure Data Backups & Networks (WiFi, VPN, etc.). Give Us a Call – 305 490 8331.

Call or email us now. info@itedatacom.us, 305 490 8331


Add a Comment